10+ dfd threat modeling
Threat modeling methods are used to create an abstraction of the system. This learning path takes you through the four main phases of threat modeling explains the differences between each data-flow diagram element.
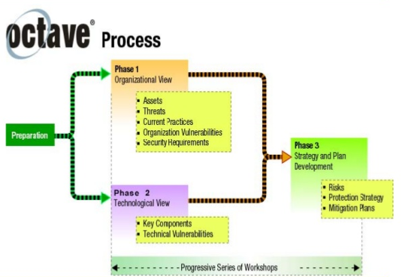
What Is Threat Modeling All You Need To Know Overview
Threat Modeling Security Fundamentals.
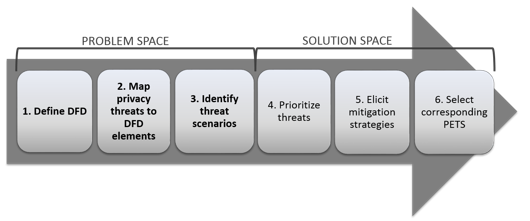
. To prevent threats from taking advantage of system flaws administrators can use threat-modeling methods to inform defensive measures. The original intent of a data flow. Threat Modeling Cheat Sheet.
The Microsoft Threat Modeling Tool 2016 will be end-of-life. Threat Modeling Process on the main website for The OWASP Foundation. There are several tools available that could be used.
Get the guide today. Numerous threat modeling frameworks exist including the popular STRIDE which was developed at Microsoft. Threat modeling is a process for capturing organizing and analyzing all of this information.
Threat modeling for IT system and application security entered the cybersecurity mainstream in the early 2000s. Profiles of potential attack-ers including their goals and methods. OWASP is a nonprofit foundation that works to improve the security of software.
OWASP Threat Dragon The OWASP Threat Dragon project is a. In this blog post I summarize 12. It is also used to produce data.
If you dont like to manually draw your DFD. The most popular Threat Modelling techniques are Data Flow Diagrams and Attack Trees. The above IoT threat modeling DFD was created per Microsofts example9 with TMT using their newest Azure and IoT template.
The change in delivery mechanism allows us to push the latest. It adopts the perspective of malicious hackers to see how much damage. Better protect your organizations data and systems with zero trust.
And a catalog of potential threats that may arise. Ad Find out why security experts are using the zero-trust model for organizational security. Microsoft Threat Modeling Tool 2016 is a tool that helps in finding threats in the design phase of software projects.
Microsoft Threat Modeling Tool. Initially the discipline borrowed its analytic concepts from. Data Flow Diagrams DFD A data flow diagram is a schematic that illustrates the flow.
Applied to software it enables informed decision-making about application security risks. It is an open-source tool that. The Microsoft Threat Modeling Tool 2018 was released as GA in September 2018 as a free click-to-download.
It identified 46 potential categorical threats. LINDDUN a privacy-centric framework. Threat modeling works by identifying the types of threat agents that cause harm to an application or computer system.
Data flow diagrams therefore are generated as a means of communicating this to the outside world those who are not threat modelers. Microsoft Threat Modeling Tool is one of the oldest and most tested threat modeling tools in the market.

ドライバーのセキュリティ チェックリスト Windows Drivers Microsoft Docs

20 Flow Chart Templates Design Tips And Examples Venngage

Pdf Security Risk Management In E Commerce Systems A Threat Driven Approach
What Are The 10 Business Process Modelling Techniques Explained With Examples Quora
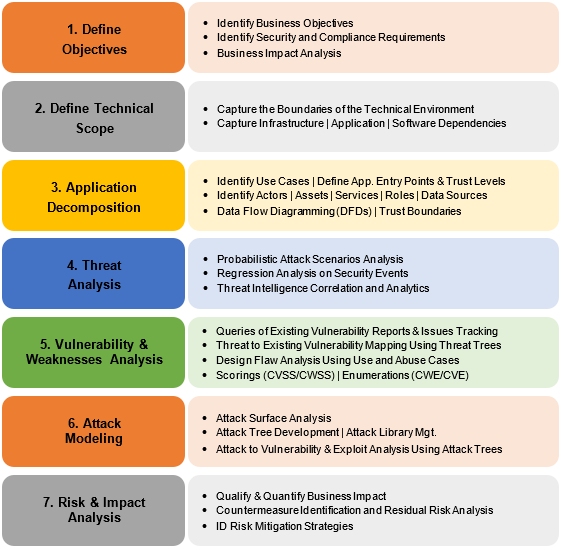
What Is Threat Modeling All You Need To Know Overview
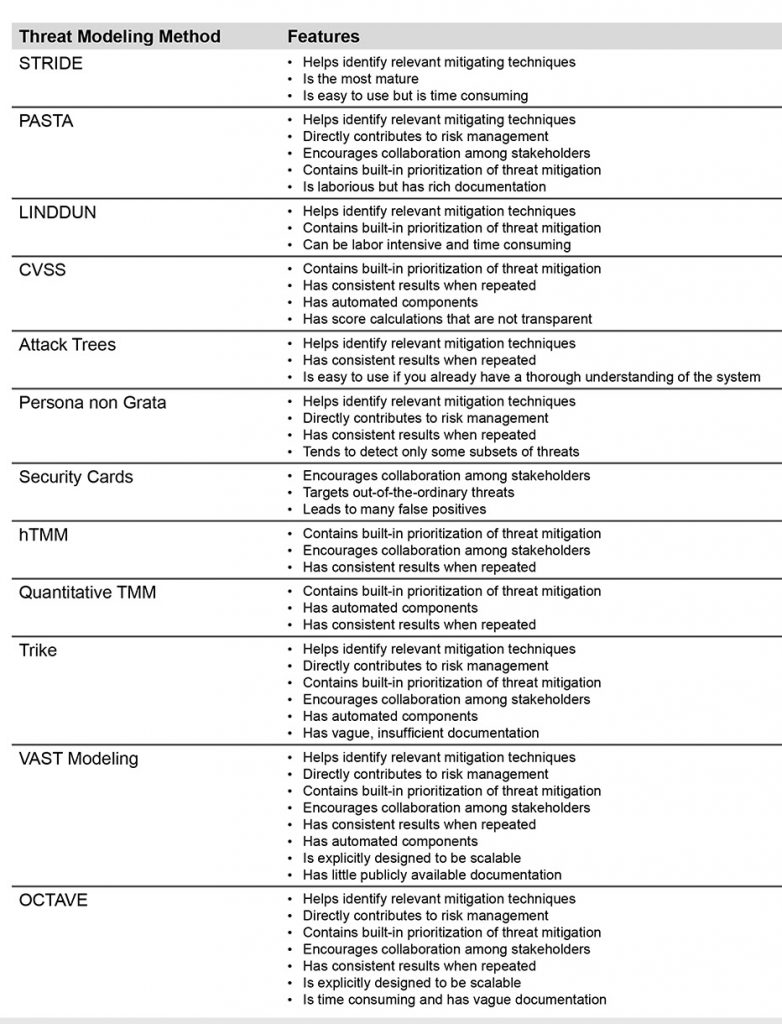
What Is Threat Modeling All You Need To Know Overview

Mobile Application Security Ppt

Hardware Platform Interface Wikiwand

Threat Modelling An Overview Knoldus Blogs
2
What Are The 10 Business Process Modelling Techniques Explained With Examples Quora

Threat Model Wikiwand

What Is Threat Modeling All You Need To Know Overview

What Is Threat Modeling All You Need To Know Overview
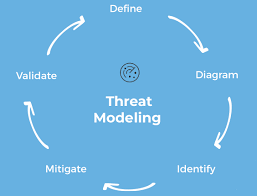
What Is Threat Modeling All You Need To Know Overview

20 Flow Chart Templates Design Tips And Examples Venngage
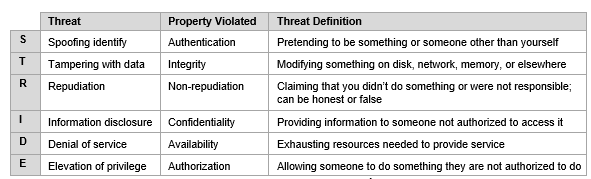
What Is Threat Modeling All You Need To Know Overview